Aftermath of a missile strike on an apartment building in Kyiv. Image: Flickr
15 Tips for Investigating War Crimes
Guide Resource
Investigating Russia and the War in Ukraine
Chapter Guide Resource
9 Best Practices for Investigating Refugee Issues
Chapter Guide Resource
Lessons Learned from Syrian Journalists Investigating Russian War Crimes
Chapter Guide Resource
Investigating Russia Around the World: A GIJN Toolkit
Chapter Guide Resource
15 Tips for Investigating War Crimes
Chapter Guide Resource
Amateur Open Source Researchers Go Viral Unpacking the War in Ukraine
Chapter Guide Resource
Essential Steps for Journalists in Emergency Situations
Chapter Guide Resource
Bellingcat’s Grozev on Investigating Russia’s Invasion of Ukraine
Chapter Guide Resource
Tips for Archiving Telegram Messages on Russia-Ukraine War
Chapter Guide Resource
Journalism Resources for Tracking Events in Ukraine
Chapter Guide Resource
10 Tips for Tracking Russian-Owned Assets
Chapter Guide Resource
Digging Into the Disinformation Campaign Behind Russia’s War on Ukraine
Chapter Guide Resource
Video: GIJC23 – Resources for Investigating Russia
Chapter Guide Resource
Video: GIJC23 – Best Investigations on Russia’s War on Ukraine
Editor’s Note: The chief prosecutor of the International Criminal Court announced this week that his office has determined there is a “reasonable basis” to open an investigation into possible war crimes in the Russia-Ukraine war.
Reporting violations in an active conflict, previously a daunting and life threatening task, has now become easier thanks to open-source reporting techniques. Thanks to much improved cameras in mobile phones, the digital media being uploaded by combatants themselves to social media and other sites online is now of a very high resolution. Couple that with the availability of high-quality satellite imagery and digital tools that let you sift through the masses of data being uploaded online, and reporters enjoy a much greater ability to investigate war crimes as they happen.
The Syrian war was the first test of this – it was the most widely documented war in human history at the time, and its unfolding was tracked online in real time. A similar situation is unfolding in Ukraine right now, so GIJN tasked me with formulating this guide to investigating war crimes using open source tools and techniques.
I’m an investigative journalist and documentary filmmaker, specializing in combining open-source techniques with fieldwork to expose human rights abuses in conflict and war. In the past four years, I have produced investigations for the BBC that uncovered war crimes in Libya and Syria; and I’ve completed a PhD on how open source intelligence is changing the future of investigative journalism.
Here, then, are 15 tips and techniques for investigating war crimes:
1. Familiarize Yourself with Types of War Crimes
The basic definition of a war crime is a violation of the rules of engagement governing a war. They are the most serious crimes committed during war, and have no statute of limitation on prosecution, which means those found guilty can be prosecuted irrespective of the historic nature of the crimes.
The Geneva Convention defined new types of war crimes and established universal jurisdiction for prosecution, and includes a major part of international humanitarian law. The International Committee of the Red Cross (ICRC) defines international humanitarian law or the law of armed conflict as “a set of rules which seek, for humanitarian reasons, to limit the effects of armed conflict. It protects persons who are not or are no longer participating in the hostilities and restricts the means and methods of warfare.” Article 7 & 8 of the Rome Statute, the founding treaty of the International Criminal Court, provides a very detailed list of war crimes and crimes against humanity.
There are four categories of war crimes: genocide, crimes against peace, violations of the customs of war, and crimes against humanity.
The key ones that can be documented using open source intelligence are: attacks on civilians and civilian infrastructure that is not being used for military purposes; attacks on protected institutions like hospitals and schools; certain types of attacks like “double tap” that target first responders; use of specific banned weapons like cluster munitions; desecration of bodies of opposing fighters and granting no quarter upon surrender; desecration of bodies of civilians; wartime sexual violence; pillaging; torture; use of child soldiers; and use of chemical or biological weapons. For certain targets, the principles of proportionality are used to assess whether such attacks can be a war crime.
2. Know the Sources
Social media is a rich source of imagery, especially uploads of videos and photos from soldiers and frontline workers, which can be evidence. Facebook, Telegram, Twitter, Instagram, TikTok are the usual suspects, but country-specific social media is better. For example, VK (formerly VKontakte) has a wealth of information from profiles of fighters in Russia. There are usually online groups of the families of fighters, or Telegram channels by fans of certain militia which are good sources. Another trick is to find accounts on multiple social media platforms using the same handle, which might have more lax privacy settings. Most of the time, the fighters don’t realize they’ve committed a war crime or don’t fear its consequences, so they don’t bother hiding it.
In a Libya investigation for the BBC, I uncovered evidence of the desecration of bodies of captured fighters and civilians by members of the Libyan National Army’s special forces brigade, through the public Facebook profiles of the perpetrators, and videos of summary executions on Twitter. They were uploading the evidence as propaganda, and using it to incite violence among their supporters online.
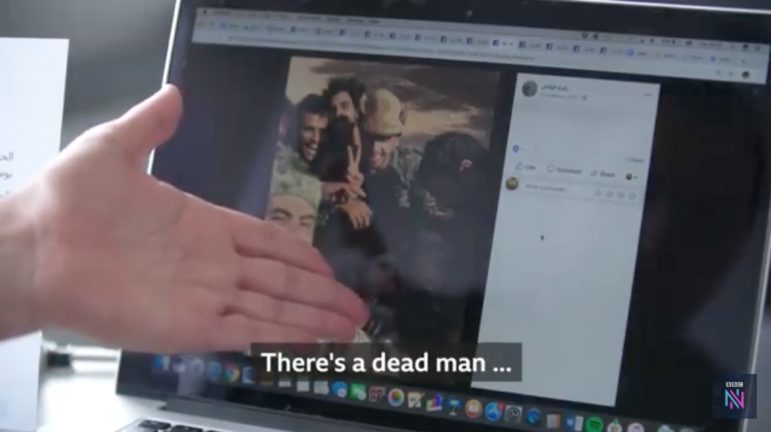
Author Manisha Ganguly was part of a BBC investigative team that used social media to track war crimes in Libya. Image: Screenshot
3. Verification
Most of the time, you will encounter the videos you find in isolation, and not from a person’s personal social media account. The key initial step is to verify using a video metadata tool to make sure it depicts what it claims to. Some tools that can help you do that are: InVid, Google Reverse Image Search, TinEye, RevEye, Yandex, Baidu, Google Lens, Exiftool, Redfin, Amnesty Video verification, and Trulymedia.
Once the authenticity of the video is established, the next step is to find supporting evidence. If other copies of the video exist online that are of higher quality, they should be downloaded as it will be easier to do facial identification from them. In addition, if other videos exist of different angles of the same incident, they are critical for reconstruction.
4. Archive Everything
The next step after verification is archiving. This is of paramount importance because there is a chance that this material can be made private or deleted by the uploader. In other instances, as in Syria and Myanmar, companies like Facebook have been guilty of removing media of atrocities and war crimes that would otherwise be necessary evidence for international prosecutions. Therefore, there is a great need to preserve the evidence as soon as possible.
When investigating a particular incident or fighter, it’s always best practice to archive everything related to the incident or on the fighter’s profile. For social media profiles of combatants, it is helpful to archive the full profile and then branch out into open friend lists to find co-combatants. Often, if you have the name of fighters and their profiles are private, there will be public profiles linked to them that you can then use to verify identity.
The tool I’ve used for archiving is Hunchly, which does it automatically and saves time. Also useful is the Wayback Machine for online archiving. I usually start with a Google spreadsheet to log links, a separate folder to download high resolution copies of media, and Hunchly running in the background to automatically archive the web pages in real time.
5. Corroboration with Eyewitnesses
Corroboration of evidence with locals on the ground is a very important but often overlooked step. This is not purely open source reporting, as I prefer to create a hybrid approach to make sure all bases are covered. It can also sometimes bring up new information, such as eyewitnesses who supply additional details to strengthen the investigation.
For example, in another BBC investigation into the murder of the only female Kurdish politician in Syria, Hevrin Khalaf, by a Turkish-backed militia, we actually managed to find an eyewitness who had found the body immediately after the murder, and who was able to fill in crucial blanks.

A BBC investigative team found an eyewitness to document the murder of Syria’s only female Kurdish politician by a Turkish-backed militia. Image: Screenshot
6. Identification
If the video depicts a specific fighter committing a war crime, identifying the fighter is critical. Facial recognition tools like Pimeyes are especially useful, but for Russia-Ukraine investigations, the best is FindClone, which is creepily good.
It was eerily accurate and helped me identify almost all Wagner mercenaries found rampaging in Libya for another BBC investigation.
7. Tracking Movements Remotely
Tracking military movements remotely using tracking tools like Marine Traffic, Flightradar24, and ADSB Exchange can also help pinpoint violations where there is plausible deniability.
For example, if a military official claims one of its jets did not bomb a specific target, its transponder data may refute that claim by placing it at that exact site at the moment of attack. (Note: pilots can turn off their transponders to avoid detection when committing possible crimes.)
8. Specialized Analysis: Military Units
When investigating violations in conflict where the perpetrators are visible on camera, two other key elements to watch out for are: insignia and weapons. Patches, other uniform insignia, and vehicle markings are useful for establishing a pattern of behavior within a specific military unit, which could help establish the culpability of war crimes up the chain of command. If soldiers from a specific unit are posting graphic violence more, it often indicates a special status of impunity. The Wiki page on military insignia is quite handy.
For my BBC investigation into Libyan war crimes, it was the Al Saiqa brigade patches that kept repeatedly showing up in these videos of graphic violence. Al Saiqa is a special forces brigade of the Libyan National Army, led by Mahmoud al-Werfalli (a commander in the brigade) who was wanted by the International Criminal Court for 33 counts of war crimes of murder and ordering the murder of non-combatants. When his warrant went public and he was still not arrested, it indicated a culture of impunity that led me to investigate the crimes of his unit.
9. Specialized Analysis: Weapons
Weapons are another key element to watch out for: what weapons are being used, where, and by whom. Some munitions, like cluster munitions, are internationally banned by a separate UN treaty. They are composed of smaller munitions that explode when airdropped and adversely impact civilians. Their use has been documented in Syria, and most recently in Ukraine by the Russian military using BM-21 Grad rockets. Some weapons databases useful to track the movements of weapons include: Janes’ database, the University of Geneva small arms database, SIPRI, and the Arms Trade Treaty.
In other cases, the use of specific weapons indicates violations of sanctions and weapons embargos. Another BBC investigation in Libya by my colleagues and I found that an attack that killed 26 unarmed cadets was actually conducted by a Chinese drone operated by the UAE – two unlikely allies in a war they should not be engaged in, violating the UN arms embargo.
10. Sexual Violence
Sexual violence, such as rape, when perpetrated in wartime by combatants is also a war crime. It is often overlooked, and there is no consensus on what constitutes wartime sexual violence, but it is one of the most commonly perpetrated war crimes.
A recent example of this is the use of rape as a weapon of war by Ethiopian National Defense Force soldiers in the Tigray war, or the rape of Rohingya Muslim women by Burmese soldiers during the Rohingya genocide.
One very helpful resource for reporting on sexual violence in conflict is this guide from Dart Center Europe. It includes tips for working in wartime and has sections devoted to self-care and how to appropriately interview and portray victims. And it offers advice on remote reporting and how to liaison with on-the-ground fixers or sources.
11. Make Note of Hospitals, Schools, and Known Civilian Targets
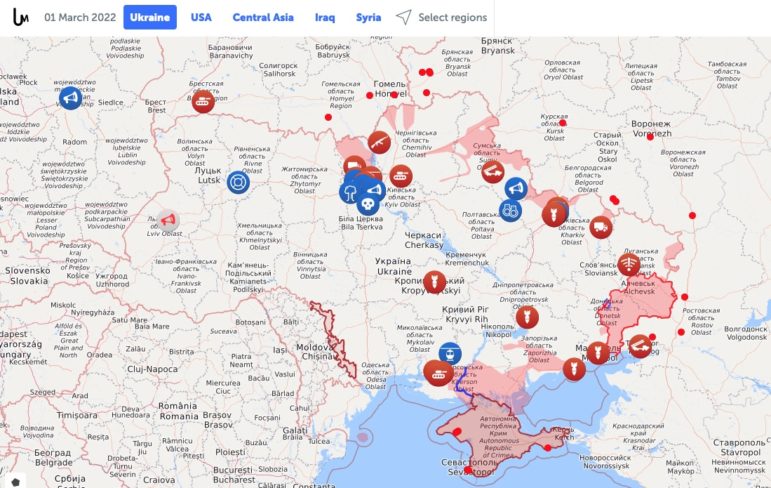
Hospitals and schools have special protections in wartime, as do civilians. Civilians must not be the target of an attack, and geolocation of open source footage can be a useful tool to determine that. Geolocation tools like Google Earth, Yandex Maps, Sentinel Hub, Echosec, and Wikimapia can help to confirm locations for verification, and Suncalc is a useful tool for chronolocation to determine the time of day of an attack (when shadows are visible). Liveuamap is a good starting point to get coordinates for these types of investigations, before branching out into satellite imagery using Google Earth. Bellingcat has some helpful guides and excellent examples of geolocation.
One example of this kind of investigation is the migrant detention center in Libya which was bombed. Ground footage from social media, and geolocation showed that the detention center was situated beside a weapons depot that had been struck two months earlier, which was confirmed by the New York Times. However, I later reported for BBC Arabic that the bombing was done by a foreign jet, violating the UN imposed arms embargo on Libya – which made it a war crime.
12. Timing is Key
Medical personnel and hospitals, as mentioned earlier, are protected by international law. So it is a war crime to target first responders, as with a “double tap” attack, when an initial bombing or raid is closely followed by a second one to specifically kill rescuers trying to help the injured. Russia has been accused of committing double tap airstrikes in Syria, most prominently on a civilian market in Idlib in 2019, which I investigated for the BBC.
Another key behavior to look for is when an invading army gives no quarter, despite visible surrender from defending forces.
13. Communication
Most of the time, soldiers committing and documenting their own war crimes are doing so because they feel protected by the powers that be. This makes them open to communication and admissions about their conduct in some instances.
After I had completed the gathering of evidence of desecration of bodies in the Ganfouda massacre in Libya, our team reached out to some of the fighters I had identified as committing these crimes, as a right of response. One of them was bragging about his conquests, claiming he was untouchable.
14. Information Security
Before reaching out to a combatant who you are accusing of a war crime, it is essential to make sure the evidence is safely backed up, and the devices used for investigation and communication are secure. There are many online resources on digital security, but the key basics involve using password management, two-factor authentication, virtual private networks, and using dummy profiles to do social media investigations. GIJN has a list of best practices.
15. Trauma Awareness
Trauma awareness is often overlooked but it is perhaps the most important part of conducting investigations into war crimes, which often involve long hours of sifting through extremely graphic imagery online. Best practices include taking regular breaks and time off, openly discussing the impact of this work with colleagues, and turning off audio when investigating graphic murder videos. For news organizations whose staff are confronting intense and violent subject matter, the Dart Center has developed a detailed, step-by-step procedure that is designed to help mitigate stress and mental anguish.
The risks of vicarious trauma from conducting this kind of work is great, and in my doctoral research interviewing 30 open source experts in the field, I found that 90% of investigators reported mental health impacts which ranged from nightmares, insomnia, depression, anxiety, social withdrawal, to serious issues like post traumatic stress disorder (PTSD) and contemplation of suicide. Managers overseeing these types of investigations must support investigators who need special help and train staff in resilience, while freelancers must make sure to self-regulate and access counselling or mental health support. Research has shown that journalists who conduct these kinds of investigations usually have a very high tolerance for graphic imagery and are naturally resilient, so they just need a supportive environment to do their best work.
Additional Resources
How to Use Data Journalism to Cover War and Conflict
Four Quick Ways to Verify Images on a Smartphone
How Open Source Experts Identified the US Capitol Rioters
Manisha Ganguly is an investigative journalist and documentary filmmaker. She currently works as a digital documentary producer for the BBC World Service’s Investigations team. Ganguly is a Forbes Under 30 media honoree, and her documentaries have won international awards and been broadcast to over 300 million worldwide.