Illustration: Marcelle Louw for GIJN
How Digital Threats Training Has Powered Innovative Cyber Investigations Around the World
From investigating a money scam sent over Whatsapp to exposing lucrative phishing accounts, alumni of GIJN’s four Digital Threats courses have produced a number of exposés of online scams and disinformation, from India to Kenya to the Philippines.
Presented by several cyber experts in a dozen remote, hands-on sessions, these courses — launched in 2023 — have trained 107 investigative journalists and researchers across four cohorts. A recent GIJN survey of 31 alumni from those cohorts found that individual alumni and their newsroom teams have subsequently published increasingly ambitious and sophisticated exposés into deeply veiled online deceptions. Follow-up interviews also revealed how the reporters behind these investigations leveraged the Digital Threats course’s new tools and techniques and bolstered their confidence to pursue seemingly impenetrable frauds. Just as follow-the-money reporters have gained much greater capacity in recent years to uncover shell company networks and hidden assets, cyber journalists are now increasingly empowered to expose digital camouflage and online misconduct.
Here are three detailed examples of recent, impactful investigations that were sharpened by GIJN’s Digital Threats training.
Exposing an Encrypted Messaging Platform Fraud (India)
Earlier in 2025, a BoomLive story by Hera Rizwan, entitled It Wasn’t Just A WhatsApp Image That Stole Rs 2 Lakhs, revealed an online money scam in India. Published by BoomLive’s Decode section, Rizwan’s story explained to readers how this complicated fraud was triggered by the seemingly harmless step of clicking on an image in a WhatsApp chat, which ultimately allowed bad actors to use steganography and malicious APK binding to gain access to people’s devices — and then drain their bank accounts. Rizwan, an alumnus from GIJN’s fourth Digital Threats course, says one of the less appreciated benefits of the training is that reporters learn how to handle malware-type evidence without the risk of being infected themselves, and develop the confidence to dig into all the relevant materials.

Hera Rizwan of BoomLive’s Decode section. Image: Courtesy of Rizwan
“Lessons from trainers like Craig (Silverman), Luis (Assardo), Jane (Lytvynenko,) and (Etienne) Maynier — on verifying sources and connecting technical details to real-world impact — guided how I structured the investigation and narrative,” she explains. “The course taught how to translate complex technical concepts into accessible language for readers, a skill I applied when explaining steganography and APK binding in the story.”
Rizwan notes that Indian media coverage of cyber scams generally focuses on just the basic facts released by police, like reporting the incident and the amount of money lost. She says her deeper understanding of the subject matter allowed her to expose “the technical and psychological layers behind the attack — how a harmless-looking image could carry hidden malware, and how scammers exploit trust and familiarity to deceive victims.”
In another innovative digital investigation, Rizwan leveraged her new skills to reveal how one of India’s largest gig economy platforms used AI to alter the photos of service professionals without their consent, and with harmful consequences.
“Beyond data privacy concerns, the story highlights how algorithmic decisions and AI-driven automation can directly impact the livelihoods of vulnerable gig workers,” she explains.
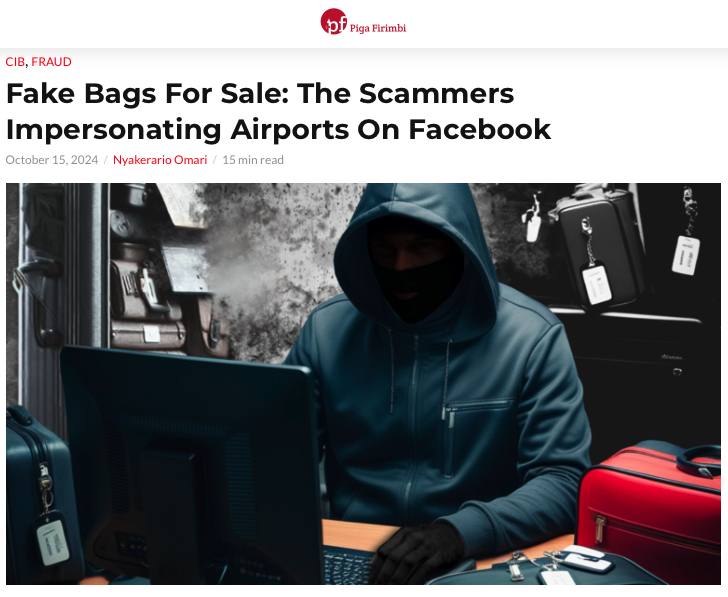
Unmasking a Facebook Airport Scam (Kenya)
In October 2024, an investigation by Nyekerario Omari, for Kenya’s Piga Firimbi, revealed how a network of Facebook accounts were impersonating airports and airlines around the globe to “sell” unclaimed passenger luggage that does not exist. Her story Fake Bags for Sale exposed 112 phishing accounts, and — similar to Rizwan’s WhatsApp story — also alerted readers about how they can recognize and avoid this type of scam.
An alumnus from the third Digital Threats cohort, Omari says her first challenge for the project was to establish relationships between the Facebook accounts without an exhaustive network analysis process. “I relied on the common tactics and techniques used by these accounts,” she explains, “such as language which created urgency about the lost luggage; claims that the listed airports were selling off valuable unclaimed bags at an affordable price; the use of common manipulated/edited images, and fake testimonials across posts.”

Nyekerario Omari is a graduate of GIJN’s third Digital Threats training cohort. Image: Courtesy of Omari
Omari says her Digital Threats training was particularly helpful with her next challenge: to deconstruct the mechanics of how the scam worked.
“Through the GIJN Digital Threats course, [I] was able to highlight how these phishing campaigns work, by digging into Facebook campaigns which rely on clickable impersonated websites with a short shelf life to collect the victim’s personal data,” she says. “The techniques used for this relied on analyzing domain data and Facebook page transparency using tools like WhoIs, DNS Checker, Big Domain Data, and Reverse image searches to establish any manipulation.”
She adds: “The tools and techniques introduced during the second week of training by Craig Silverman were new for me, along with the fundamentals of investigating digital threats.”
She also points out that the training provided her valuable “backup tools” to have on hand for this and other investigations — alternate methodologies that she can try when a familiar tool fails to produce results.
“Most of the tools shared complemented each other,” she notes. “For example, DNSLytics, DNS Checker, and Big Domain data complemented WhoIs [search]. Additionally, InVid WeVerify and Photo Forensics proved valuable when a page’s transparency offered limited information.”
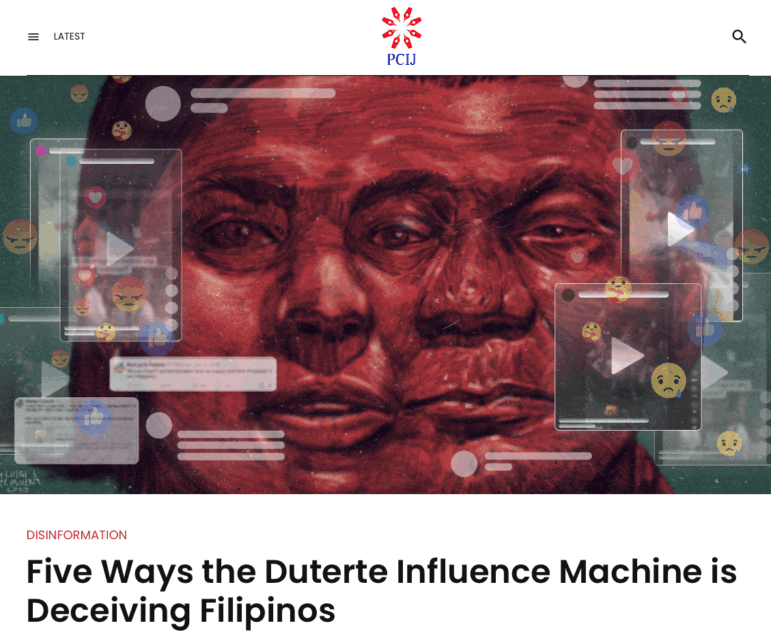
Revealing a ‘Cyborg’ Disinformation Campaign from News Comments Analysis (Philippines)
In August of this year, Philippine Center for Investigative Journalism (PCIJ) reporter Regine Cabato, uncovered a “cyborg” propaganda operation, in which a mix of humans and AI-driven bots were peddling coordinated misinformation across the Internet in support of that country’s Duterte family dynasty.

PCIJ reporter Regine Cabato. Image: Courtesy of Cabato
An alumnus from GIJN’s 2024 Digital Threats training, Cabato says one impact of the story was to help inoculate readers against this wave of disinformation. Its reach was also impressive, as a social media video version of the story received 130,000 views across Facebook, Instagram, and TikTok. The exposé also triggered a retaliatory harassment campaign against PCIJ from extreme pro-Duterte supporters, later described in a story by Rappler.
“My co-author Giano Libot and I have kept abreast of partisan influencers, then started comparing notes on the trends we noticed,” says Cabato. “One of the things we noticed was how thousands of suspicious accounts would use “scripts” — recurring arguments with repetitive keywords — in the comment sections of mainstream newsrooms’ posts about Duterte-related news, usually within an hour of posting. I bookmarked one of these posts when I first noticed the trend.”
“For the comment section analysis, Giano used an Apify tool for initial scraping of a sample size of some 2,000 comments. I learned about the tool via the GIJN training,” Cabato says, adding that “Who Posted What? was another helpful tool she learned about in the Digital Threats course.
 Rowan Philp is GIJN’s global reporter and impact editor. A former chief reporter for South Africa’s Sunday Times, he has reported on news, politics, corruption, and conflict from more than two dozen countries around the world, and has also served as an assignments editor for newsrooms in the UK, US, and Africa.
Rowan Philp is GIJN’s global reporter and impact editor. A former chief reporter for South Africa’s Sunday Times, he has reported on news, politics, corruption, and conflict from more than two dozen countries around the world, and has also served as an assignments editor for newsrooms in the UK, US, and Africa.