

An Online Survival Kit from Reporters Without Borders
How can you protect yourself from online snooping? Reporters Without Borders has published an Online Survival Kit on its WefightCensorship.org website with tools and practical advice that will help protect your communications and data. As the website explains, “The tools and techniques presented in this kit do not require advanced knowledge of computers and programming.” In other words, you don’t need to be an IT engineer to protect your emails and stay anonymous online.
The Reporters Without Borders Digital Survival Kit is available in French, English, Arabic, Russian, and Chinese, and is published under a Creative Commons license. Here are excerpts from the guide:
ONLINE SURVIVAL KIT
FIFTEEN MINUTES OF ONLINE ANONYMITY
Making sure that your communications and data are confidential is not easy. Many encryption tools are available but it can take ages to learn how to use them, to learn how to avoid leaving clues or tracks that will allow others to intercept a message or identify who sent it. So that you don’t have to spend the next three years training to become a security expert, Jean-Marc Manach, a journalist specialized in digital privacy and security, has an interesting alternative – how to have 15 minutes of online anonymity.
 A PRACTICAL GUIDE TO PROTECTING YOUR IDENTITY AND SECURITY WHEN USING MOBILE PHONES
A PRACTICAL GUIDE TO PROTECTING YOUR IDENTITY AND SECURITY WHEN USING MOBILE PHONES
Many activists have been tracked via their mobile phones, and some countries conduct surveillance more extensively than others. You need to assess the risk for your own activities given the practices used in your country, how high-profile your work is, and what others in your community have experienced. Here’s a guide to protecting your phone.
 TAILS: THE AMNESIC INCOGNITO LIVE SYSTEM
TAILS: THE AMNESIC INCOGNITO LIVE SYSTEM
Tails is an operating system like Windows or Mac OS, but one specially designed to preserve your anonymity and privacy. It allows you to use the Internet anonymously almost everywhere online and on any computer, but leaves no trace of what you have done, unless you want to. Here’s more on Tails.
 SENDING ENCRYPTED EMAILS USING THUNDERBIRD AND PGP
SENDING ENCRYPTED EMAILS USING THUNDERBIRD AND PGP
More than 200 billion e-mails are sent worldwide every day. Although it is a very practical tool for exchanging information, it is also vulnerable and users can encounter problems such as interception, identity theft and monitoring. Yet there are easy ways to ensure your Internet activities remain confidential. Read more here.
This technology, widely used in the business world, allows the creation of an Internet tunnel (a virtual link) between two physical networks in different locations in a way that is transparent for users. Only they will by allowed access (hence the term “private”) and data sent via the tunnel is encrypted. This guarantees that data sent by VPN users will be illegible to any third party in the event of malicious interception such as espionage or intrusion. Here’s more on VPN.
METADATA – YOUR FILES TALK FOR YOU
Did you know this? When you send a document, a lot of data goes with it. But few Internet users are aware that many file formats contain hidden data, or metadata. Text processing files or PDFs are likely to contain the name of the author, the date and time of the creation of the file, and often even part of its editing history. The hidden data depend on the file format and the software used to create it. Here’s more on dealing with metadata.
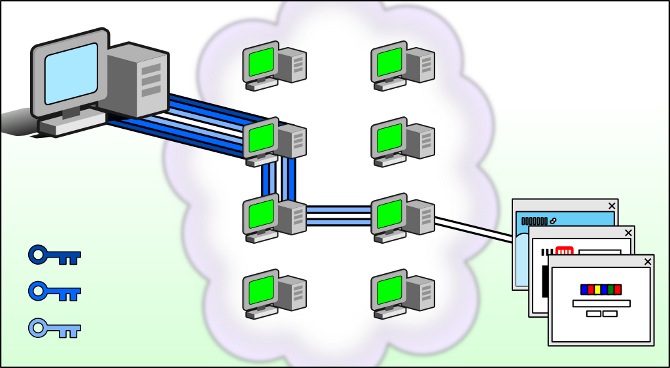 IMPROVE YOUR PRIVACY AND SECURITY ON THE INTERNET USING TOR
IMPROVE YOUR PRIVACY AND SECURITY ON THE INTERNET USING TOR
This user manual contains information about how to download Tor, how to use it, and what to do if Tor is unable to connect to the network. If you can’t find the answer to your question in this document, email help@rt.torproject.org.










